🚨 Web police 🚨
We are all concerned about the security and protection of our data. But are you really aware of what you need to do? Of what you risk?
Have you ever heard of the CNIL? I've always had the feeling that it's the villain in movies: you think in real life, it shouldn't catch you. But it still scares you.
I think I've never really wanted to delve into it because it often rhymes with lawsuits and fines... And as a developer, it can ruin your career. Or just give yourself a headache. 🤯
Maybe you're reading this, and you've never heard of the CNIL, and now I might be scaring you..?
In theory, it's pretty cool! The CNIL is like a guardian that ensures our data on the web is treated with respect, by the law. It ensures that companies, startups, and even small websites use data in a transparent, ethical, and secure manner.
Who is concerned?
You are! As a user, as a developer, as a client, whether you're French or not... It's not just about understanding how to avoid fines; it's about grasping why data protection matters and what's at stake. Whether you're a developer or entrepreneur, you bear responsibilities regarding user data. There are laws; you can't just do anything you want. As a user, it's crucial to know your rights and understand the implications of sharing your data with a service. It's an ethical matter worth contemplating, taking a step back.
What does it matter to you? With your data, a lot of things can be done, including stealing your identity, harassing you, stealing your money, selling your data, and it can then be used for malicious purposes... And these are just a few examples.
As a No-Code developer, I've noticed that the biggest concern for those unfamiliar with the ecosystem revolves around app security and data handling. Often, developers (and others) aren't fully aware of the complexities surrounding these issues.
So, together, let's take a closer look.
The next time someone questions whether secure and data-respecting applications can be built on Bubble, you'll have plenty of convincing arguments!
What are the risks?
I know you, you'll never read the checklist and the legal articles that follow unless you feel a little threatened. So here's what could happen to you if you don't follow the rules and get caught:
Fines: Imagine a fine of up to €20 million. Well, I'm exaggerating, that's in the worst case. But be aware that you can receive a fine if you don't adhere to the rules. The amounts are determined based on the context and circumstances.
Collateral damage: What about your reputation in all of this? News about CNIL rule violations spreads quickly, as you've probably heard with the scandal around Droite au cœur. Even my friends who had never heard of No-Code heard about it; it went viral on Twitter (or X, sorry).
🗞For those who haven't heard about this story, it involves a dating site that was developed on Bubble. The privacy rules were not correctly implemented, and it was possible to access certain sensitive user data, such as their name, sexual orientation, gender...Legal troubles: If the CNIL doesn't catch you, the users will. They can sue you for mishandling their data.
And now you're wondering, is it me, the small Bubble freelancer, or the company that will suffer?
To put it simply, if the company asks you to develop something that is not in compliance, it's the company that will be held responsible. That's what we call the data controller. But now that you know all of this, you can explain to them what they risk, and it would be a good idea to refuse to develop such features.
The developer acts according to the company's instructions. But imagine you develop an app, and in reality, it's not in compliance, but the company wanted it to be. In that case, it's your fault, and you are considered the data controller.
CNIL & Bubble: How to go about it?
Here are the things to know and the steps to take to comply with the rules:
User Information:
- Ensure you inform users about how their data will be used, stored, and shared. This typically includes a detailed and accessible privacy policy.
Create a dedicated page for the privacy policy and terms of use, and use elements like pop-ups or banners to inform new users and obtain their consent.
Consent:
Obtain clear and explicit consent from users before collecting their data.
Consent can't be presumed (e.g., an unchecked checkbox).
Users should be able to withdraw their consent as easily as they gave it.
Include checkboxes during registration or on specific forms where data is collected.
Ensure these checkboxes are not pre-checked.
Set up workflows to capture and store consent.
Data Minimization:
Only collect data that is strictly necessary for your application's operation.
Limit the data retention period to what is strictly necessary (I attached a guide for determining the data retention period at the end of the article)
When designing the database, create only the necessary fields.
Example: processing support requests.
To process this request, it will be imperative for me to collect the person's email address so that they can send me the request and for me to respond to them. The data is therefore necessary. Conversely, for the same purpose, I request the phone number even though I do not offer telephone support; the data is not necessary.
Set up workflows to automatically delete or archive data that is no longer needed after a certain period.
Security:
Implement security measures to protect personal data from unauthorized access, loss, and leaks.
This includes data encryption, server security, and the use of secure data transfer protocols.
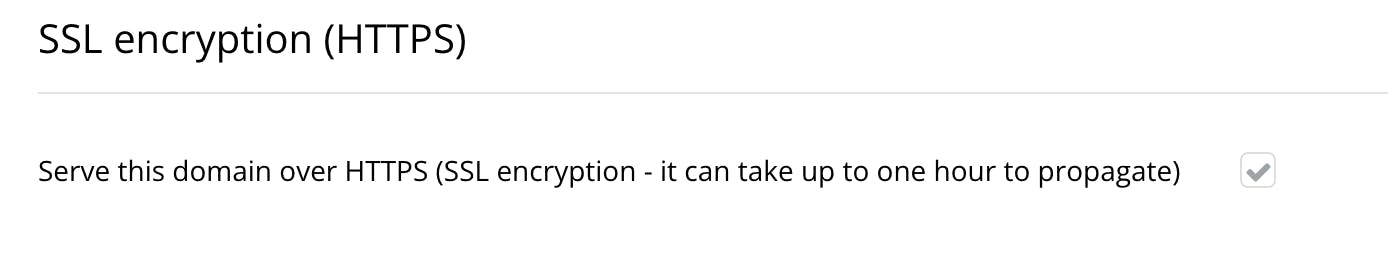
Use Bubble's built-in security features, such as SSL (a default checkbox in your settings)
In Settings > Domain/Email
Limit access to data in your database to appropriate users or roles.
Protect your data thanks to the famous PRIVACY RULES: That should be one of your biggest concerns.
Ensure that the plugins or external APIs you use are secure.
For that, request a privacy policy, contact the developer, and inspect the code (contact the developer 🤪).
User Rights:
Ensure that users can exercise their rights under the GDPR and the Data Protection Act, including the right of access, rectification, erasure ("right to be forgotten"), processing restriction, and data portability.
💡The French Data Protection Act, enacted in 1978 and amended several times, governs the protection of personal data, outlining rights and obligations related to the collection, processing, and storage of personal information to safeguard individuals' privacy.
For the bravest among you, you will find a brief reminder of the relevant articles concerning GDPR at the end of the article.
Create pages or sections in your application where users can view their data.
For the right to erasure or data portability, implement specific workflows that allow users to delete their accounts or export their data.
For rectification, allow users to edit their information through their profile or a dedicated form
Data Breach Management:
- Establish procedures for detecting, reporting, and investigating personal data breaches.
A few examples :
Detection: Regularly review system logs and access records for any anomalies. Educate staff to recognize and report suspicious activities.
Reporting: Immediately report any suspected data breach to the designated Data Protection Officer (DPO) or relevant responsible personnel. Provide a preliminary assessment of the breach, including affected data and potential impact.
Investigation: Document the findings and implement corrective measures to prevent future breaches.
Sub-Processors and Data Transfers:
- If you use services to process personal data (payment services, email marketing services...), ensure they also comply with the GDPR.
For example, if you use payment services or even email services to manage your emails, it is important to ensure that they don't mishandle the data you provide to them.
For that, you can check their privacy policy, or contact support directly; sometimes, it's simpler!
- Data transfers outside the EU must meet GDPR-specific requirements.
Processing Register:
Keep a record of all personal data processing activities you perform.
Clarification for companies with fewer than 250 employees. They are allowed to register only the following processes in the record:
Recurrent processes (payroll, customer management, etc.).
Processes that may pose a risk to the rights and freedoms of individuals (e.g., geolocation, video surveillance).
Processes involving sensitive data (health, criminal offenses).
Outside of Bubble, maintain a detailed document describing all data processing activities you carry out, including purposes, retention periods, etc
You need a list of data processes :
| Process | Number | Finality | Creation date | Last modification date | Sensitive data? |
| Payment Processing | 1 | Handling payment transactions securely | 12/11/2023 | 12/11/2023 | Yes |
| Newsletter subscription | 2 | Sending newsletters | 12/11/2023 | 12/11/2023 | No |
And for each process, something like :
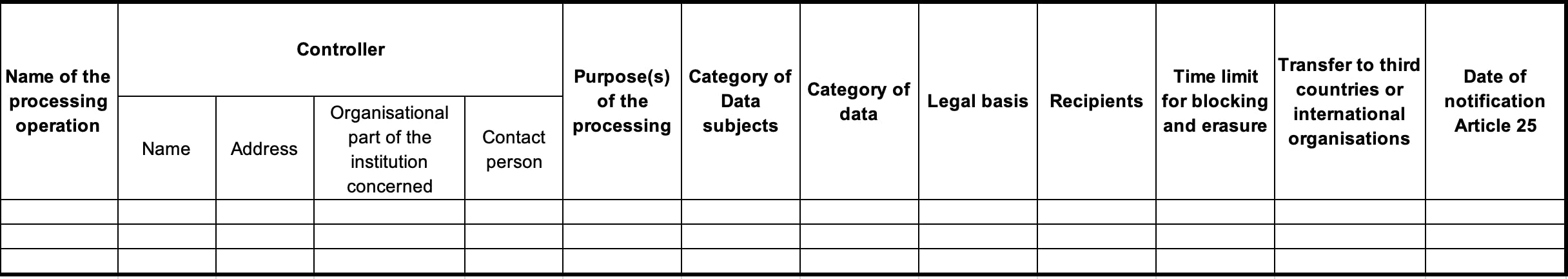
Here are the details to provide:
The name and contact information of the joint controller of the implemented processing (if applicable).
The purposes of the processing.
The categories of individuals concerned (client, prospect, employee, etc.).
The categories of personal data (examples: identity, marital status, banking information, login data, location data, etc.).
The categories of recipients to whom the personal data have been or will be disclosed, include subcontractors.
Transfers of personal data to a third country or an international organization, and, in some cases, the safeguards provided for these transfers.
The retention period.
Where possible, a general description of the technical and organizational security measures implemented.
Example: Customer management process
Joint Controller:
Joint controller: XYZ Company
Contact information: John Doe, Chief Privacy Officer, xyzcompany@example.com
Purposes of Processing:
- Customer relationship management, including order processing, communication, and support.
Categories of Individuals Concerned:
Clients (existing customers)
Prospects (potential customers)
Employees involved in customer management activities
Categories of Personal Data:
Identity: Name, address, contact details
Marital status: Optional for personalized communication
Banking information: Limited to transaction processing
Login data: Username, password
Location data: Address for delivery and service optimization
Categories of Recipients:
Internal recipients: Sales department, customer support
External recipients: Shipping partners, payment processors
Subcontractors: IT service providers for database maintenance
Transfers of Personal Data:
Limited transfers to third countries for order fulfillment.
Safeguards: Standard contractual clauses in place with international shipping partners.
Retention Period:
- Customer data is retained for 5 years after the last transaction or interaction.
Security Measures:
Technical measures: Encrypted databases, secure servers for data storage.
Organizational measures: Access restricted to authorized personnel, regular training on data protection policies.
If relevant to the size and nature of your processing, appoint a Data Protection Officer (DPO) to oversee GDPR compliance. While not always mandatory, it's advisable to have a point of contact for these matters. Mandatory only if:
Public authorities and bodies;
Private organizations whose core activities involve regular and systematic monitoring of individuals on a large scale (e.g., behavioral advertising);
Private organizations whose core activities involve processing sensitive data or data related to criminal convictions and offenses on a large scale
Are you already in trouble?
The most serious violations include, among others:
Not having the appropriate consent to process data.
Violation of the fundamental rights of the data subjects, such as the right to access and the right to be forgotten.
Transferring personal data to a third country or international organization that does not provide adequate protection.
Are taken into account:
The nature, seriousness, and duration of the violation
The actions taken by the company to mitigate the harm
If the company has previously violated the GDPR
Cooperation with the CNIL
The CNIL and all these regulations aren't there to make your life difficult; quite the opposite. It's here to ensure that users' data is treated with care and respect, yours too by the way.
As developers, we must inform our clients. Indeed, they may not necessarily come from a tech background and might not be aware of certain regulations or responsibilities they have. Aside from avoiding potential fines, it is crucial to be mindful of how we handle our users' data.
After all, we are users ourselves, so let's apply the rules that we would like to see applied to us!
Feel free to reach out if you have any questions or encounter challenges in your data-protection-related journey
Happy No-Coding 🌟
A quick reminder of the GDPR articles relevant here:
Right of Access (Article 15 of the GDPR):
- Individuals have the right to confirm whether their data is being processed and to access that data. They also have the right to obtain a copy of the processed data.
Right to Rectification (Article 16 of the GDPR):
- If the personal data held by the data controller is inaccurate or incomplete, the data subject has the right to request its correction or completion.
Right to Erasure (or "right to be forgotten," Article 17 of the GDPR):
- Individuals can request the deletion of their data in certain circumstances, e.g., when the data is no longer needed for the purposes for which it was collected, or if processing is based on consent and the individual withdraws that consent.
Right to Restriction of Processing (Article 18 of the GDPR):
In certain conditions, individuals can request the restriction of their data processing. This applies, for example, when data accuracy is contested, or when processing is unlawful, and the individual opposes data erasure, instead requesting the limitation of its use.
💡The data must be 'frozen,' meaning they should be preserved but not used
Right to Data Portability (Article 20 of the GDPR):
Data subjects have the right to receive their personal data provided to a data controller in a structured, commonly used, and machine-readable format. They also have the right to transmit this data to another data controller, with the original data controller not hindering the transfer.
💡Can only be implemented if the processing is based on the person's consent or a contract AND the processing is carried out using automated processes. Can only concern the following data: data provided by the person OR data generated by their activity
Right to Object (Article 21 of the GDPR):
Individuals have the right to object, at any time, on grounds relating to their particular situation, to the processing of their personal data, including processing based on the legitimate interests of the data controller or the performance of a task carried out in the public interest.
💡However, the controller may justify their refusal to this objection in certain cases, e.g., a contract, legal obligation...
Right Not to be Subject to Automated Decision-Making (Article 22 of the GDPR):
Individuals have the right not to be subject to a decision based solely on automated processing, including profiling, under certain conditions specified by the GDPR.
💡In practice, the individual concerned can request to be informed that a fully automated decision has been made against them, ask to know the criteria that led to the decision, challenge the decision, and request human intervention
Notification Obligation Regarding Rectification or Erasure of Personal Data (Article 34 of the GDPR):
If a personal data breach is likely to result in a high risk to the rights and freedoms of the data subjects, the data controller must notify the data subject without undue delay.
💡More specifically: the data controller must document all data breaches, but if it is likely to result in a risk, it must be reported to the CNIL within 72 hours, and if the breach is likely to result in a high risk, the affected individuals must be notified (Article 33 GDPR).
Resources
Register template: https://edps.europa.eu/data-protection/our-work/publications/other-documents/register-template-0_en
Guide for determining the data retention period https://www.cnil.fr/sites/cnil/files/atoms/files/guide_durees_de_conservation.pdf
Data protection worldwilde https://www.cnil.fr/fr/la-protection-des-donnees-dans-le-monde

